-
Popular Resistance Seizes Asian Cyber Fraud Center in Myanmar

A coalition of insurgent groups in Myanmar, situated in Southeast Asia and sharing borders with Bangladesh, India, Thailand, Laos, and China, has successfully gained control of Laukkai, a city known as a significant hub of cyber fraud in the region affecting neighboring countries.
Initiated as “Operation 1027” in late October 2023, the coalition aimed to liberate the people from the military junta that seized power in Myanmar in 2021. On the night of January 4, the government handed over control of the Kokan region, encompassing Laukkai, to the Alliance of the Three Brotherhoods.
Throughout the operation, the rebel coalition has expressed its commitment to eliminating organized fraudulent activities thriving under the watchful eye of local law enforcement loyal to the ruling junta. The rebels stated, “To eradicate telecommunications fraud, fraudulent dens, and their sponsors nationwide, including the border areas of China and Myanmar, our coalition forces have undertaken this military operation.”
This emphasis on combating fraud appears to be a strategic move to garner support from China, tired of being targeted in “pig slaughter” scams, where online fraud victims are coerced into becoming internet scammers. Human trafficking, prevalent in the region, often leaves individuals with limited alternatives.
Over the weekend, junta leader General Min Aung Hlaing met with Chinese Vice Foreign Minister Sun Weidong in Naypyidaw to discuss the common border and organized crime. The Ministry of Foreign Affairs stated that both sides agreed to jointly maintain peace, combat cross-border crime, particularly telecommunications fraud, and promote regional peace and development.
China’s Public Security Minister held a virtual meeting with Myanmar’s Interior Minister, pledging to deepen cooperation to ensure security and stability in border areas, specifically targeting telecommunications and online fraud, according to China Daily.
In August 2023, the UN estimated that around 120,000 people in Myanmar were recruited for fraudulent operations. In January 2024, Chinese state media reported that approximately 41,000 individuals involved in telecommunications fraud in Myanmar had been handed over to Chinese authorities in the past year. The exact nature of these detainees, whether victims of human trafficking or cyber scammers, remains unclear.
Despite the insurgency’s success, cybersecurity experts warn that fraudulent activities may relocate to other parts of the country, particularly along the borders with Thailand and Laos. Peng Deren, commander of the Myanmar National Democratic Alliance Army, noted in an online New Year’s speech that such moves were already occurring, with military helicopters evacuating fraud leaders and families to enclaves along the Thai border.
-
Turkish Hackers Target Unsecured MS SQL Servers Worldwide: Protect Your Data

A financially motivated campaign targeting inadequately secured Microsoft SQL (MS SQL) servers has been detected in the U.S., Latin American (LATAM) regions and European Union. Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov reported that the ongoing threat campaign, associated with actors of Turkish origin, has been dubbed RE#TURGENCE.
According to the researchers, the campaign concludes by either selling “access” to the compromised host or deploying ransomware payloads. The initial breach involves brute-force attacks on servers, followed by the utilization of the xp_cmdshell configuration option to execute shell commands on the compromised host. This methodology resembles a previous campaign named DB#JAMMER, which surfaced in September 2023.
Following this, a PowerShell script is retrieved from a remote server to fetch an obfuscated Cobalt Strike beacon payload. The post-exploitation toolkit is then employed to download the AnyDesk remote desktop application from a network share, facilitating access to the machine. Additional tools, such as Mimikatz for credential harvesting and Advanced Port Scanner for reconnaissance, are downloaded.
Lateral movement within the network is achieved through the use of PsExec, a legitimate system administration utility capable of executing programs on remote Windows hosts. The attack chain ultimately culminates in the deployment of Mimic ransomware, a variant previously identified in the DB#JAMMER campaign.
While the initial infiltration methods are similar, Kolesnikov noted that DB#JAMMER was slightly more sophisticated, employing tunneling. In contrast, RE#TURGENCE is more targeted, relying on legitimate tools like AnyDesk and remote monitoring and management to blend in with normal activity.
Securonix identified an operational security (OPSEC) oversight by the threat actors, allowing them to monitor clipboard activity due to the enabled clipboard sharing feature of AnyDesk. This revealed the attackers’ Turkish origins and the online alias “atseverse,” corresponding to a profile on Steam and a Turkish hacking forum called SpyHack.
The researchers emphasized the importance of not exposing critical servers directly to the internet, as RE#TURGENCE attackers were able to successfully brute force their way into servers from outside the main network.
-
Lumma Stealer Lurks in YouTube Videos: Stay Safe by Avoiding Pirated Software

Threat actors are now using YouTube videos featuring content related to cracked software as a means to lure users into downloading Lumma, an information-stealing malware, according to a recent analysis by Fortinet FortiGuard Labs researcher Cara Lin. These YouTube videos often showcase content associated with cracked applications and provide users with installation guides, incorporating malicious URLs that are frequently shortened using services like TinyURL and Cuttly.
This tactic is not new, as previously observed attack chains on YouTube delivered various types of malware, including stealers, clippers, and crypto miners. By employing this method, threat actors can exploit compromised machines for information and cryptocurrency theft, as well as unauthorized mining.
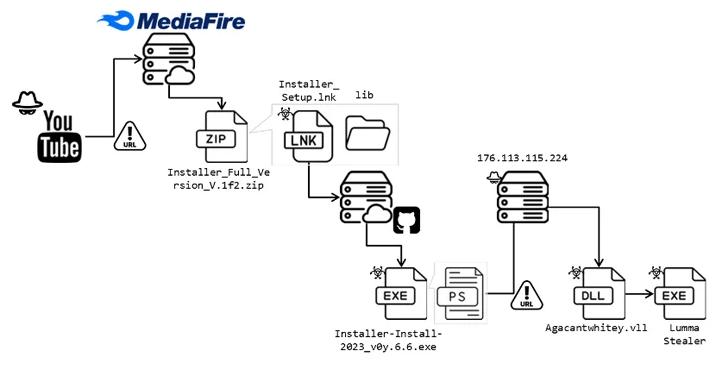
In the most recent attack documented by Fortinet, users searching for cracked versions of legitimate video editing tools, such as Vegas Pro, on YouTube are encouraged to click on a link in the video’s description. This link leads to the download of a deceptive installer hosted on MediaFire. Once unpacked, the ZIP installer contains a Windows shortcut (LNK) posing as a setup file. This shortcut downloads a .NET loader from a GitHub repository, which then loads the Lumma Stealer payload after performing anti-virtual machine and anti-debugging checks.
Lumma Stealer, written in C and available for sale on underground forums since late 2022, is capable of harvesting and exfiltrating sensitive data to a server controlled by the threat actor.
This development coincides with Bitdefender’s warning about stream-jacking attacks on YouTube, where cybercriminals hijack high-profile accounts through phishing attacks. These attacks deploy the RedLine Stealer malware to extract credentials and session cookies, ultimately promoting various crypto scams.
Additionally, an 11-month-old AsyncRAT campaign has been discovered, utilizing phishing lures to download an obfuscated JavaScript file. This file is then used to deploy a remote access trojan. AT&T Alien Labs researcher Fernando Martinez noted that the campaign carefully selects victims and their companies to amplify its impact, with some identified targets managing key infrastructure in the U.S.
-
NoName DDoS Attacks Disrupt Ukrainian Government Services

Allegedly, the NoName ransomware group has targeted various Ukrainian government websites, causing disruptions for entities such as Accordbank, Zaporizhzhya Titanium-Magnesium Plant, State Tax Service, Central Interregional Tax Administration, Tax Administration Western Interregional and the Central Office of the State Tax Service in Kyiv.
The affected websites, linked to the NoName ransomware group, experienced connectivity issues, displaying error messages like “403 Forbidden.” The group published a list of their latest victims on their dark web leak portal, with screenshots shared on Twitter. The dark web post contained a message stating, “We continue to nightmare Ukrainian sites (evil emoji).”
Several Ukrainian government websites, including those of the State Tax Service, Central Interregional Tax Administration, Western Interregional Tax Administration, and the Main Directorate of the State Tax Service in Kyiv, showed bad gateway and error messages.

Notably, the Accordbank website exhibited a “403 Forbidden” error message. Similarly, the Ukrainian State Tax Service website displayed a message indicating it couldn’t be reached, with a screenshot provided.
Given the interconnectedness of the websites, it appears that the NoName ransomware attack on Ukraine’s State Tax Service has also impacted the linked sites. The ongoing cyber conflict between Russia and Ukraine has seen hacktivist groups on both sides targeting each other, either with government backing or as acts of cyber patriotism.
Prior to the reported NoName ransomware attack on Ukraine, the same hacker collective targeted multiple Finnish government websites. On the dark web, the group declared, “Finland continues to receive our New Year’s gifts (evil smile emoji),” indicating an attempt to disrupt critical infrastructure and cause chaos for Finnish citizens. The Finnish victims of NoName DDoS attacks were exclusively government organizations associated with transport facilities.
-
LockBit Ransomware Breach Rocks Capital Health, Patient Data at Risk

The LockBit ransomware group has admitted to orchestrating a cyberattack on the Capital Health hospital network in November 2023 and is now threatening to release pilfered data and negotiation transcripts by tomorrow.
Capital Health, a prominent healthcare service provider in New Jersey and parts of Pennsylvania, manages two major hospitals along with several satellite and specialty clinics. Following a cyberattack on its network last November, the organization experienced an IT systems outage, anticipating a disruption in operations for at least a week.
In a recent security incident notification on the Capital Health website, the organization reported that all systems have been successfully restored, operations are back to normal, and additional security measures have been put in place to prevent future incidents.
Capital Health is currently investigating whether any data was compromised during the cyberattack. The LockBit ransomware gang has now asserted responsibility for the attack by including the healthcare company on its data leak extortion portal.
The cybercriminals claim to have seized seven terabytes of sensitive medical data, which they intend to release tomorrow unless the organization meets their ransom payment demands. Notably, LockBit has a policy allowing its affiliates to steal data for extortion rather than encrypting files on hospital networks. Despite similar policies being breached by other groups, LockBit states that, in the Capital Health attack, they deliberately refrained from encrypting files to avoid interference with patient care, focusing solely on data theft.

LockBit has targeted healthcare networks multiple times, including the SickKids children’s cancer hospital, the Katholische Hospitalvereinigung Ostwestfalen (KHO) in Germany, and the Carthage Area Hospital and Claxton-Hepburn Medical Center in upstate New York.
While LockBit and other cybercriminal groups adopt a data-theft approach, emphasizing extortion without encrypting infrastructure, it’s crucial to recognize the potential impact. Encryption-less ransomware attacks can still result in system outages, catastrophic data breaches for patients, and substantial financial losses for already strained healthcare institutions. Notably, the healthcare sector has witnessed various high-impact ransomware attacks, affecting organizations like Ardent Health Services, Integris Health, ESO Solutions, and the Fred Hutchinson Cancer Center (Fred Hutch).
-
Major US Mortgage Lender loanDepot Hit by Ransomware Attack

The U.S. mortgage lender loanDepot has confirmed that the recent cyber incident reported over the weekend was indeed a ransomware attack, resulting in data encryption. loanDepot, a significant nonbank mortgage lender in the United States, managing over $140 billion in loans and employing around 6,000 staff, faced disruptions when customers encountered difficulties accessing the payment portal on Saturday for loan payments and contacting the company via phone.
In response to the incident, loanDepot issued a statement acknowledging the cyber incident and the temporary shutdown of specific systems. The company assured that efforts were underway to restore normal business operations swiftly and to understand the full extent of the incident. External cybersecurity experts were engaged, and regulatory and law enforcement agencies were promptly notified.
Despite the security breach, loanDepot informed customers through social media that recurring automatic payments would still be processed, albeit with delays in reflecting on payment history. However, new payments through the servicing portal were temporarily disabled, prompting affected customers to seek assistance from the call center.
In an 8-K filing with the U.S. Securities and Exchange Commission, loanDepot disclosed that the attackers had also encrypted files on compromised devices. However, the identity of the ransomware group responsible for the attack remains unclear. The company, in its ongoing investigation, determined unauthorized access to certain systems and data encryption as part of the breach. LoanDepot is assessing the incident’s impact and its potential material impact on the company.
The incident led loanDepot to take precautionary measures, including the shutdown of some systems to prevent the attackers from accessing other devices on the network. While the company has emphasized unauthorized access and file encryption, it’s important to note that ransomware groups increasingly steal corporate and customer data during breaches to exert pressure on victims to pay a ransom.
Given loanDepot’s possession of sensitive customer information, such as financial and bank account details, individuals affected by the breach are urged to remain vigilant against potential phishing attacks and identity theft attempts. This incident follows loanDepot’s disclosure of a data breach in May 2023, stemming from a cyberattack in August 2022, and aligns with similar cybersecurity challenges faced by other entities in the mortgage and financial sectors, such as Mr. Cooper and First American Financial Corporation.
-
23andMe Accused of Blaming Users for Data Breach

23andMe, the DNA testing company, is pushing back against allegations regarding a data breach of highly sensitive genomics data on its systems last year, contending that users are at fault for the security lapse. In response to Tycko & Zavareei LLP, the law firm representing victims in a class action lawsuit filed in November 2023, 23andMe argued that users whose accounts were compromised were “negligently” responsible for the breach due to their practice of recycling and failing to update passwords.
According to 23andMe, this negligence allowed attackers to initiate a credential stuffing campaign by using usernames and passwords obtained from unrelated security breaches on other websites. The company asserted that the incident was not a result of its failure to uphold reasonable security measures under the California Privacy Rights Act (CPRA).
The data breach, which occurred in October 2023, affected nearly 7 million customers, compromising information including genealogy details such as ethnicity and ancestry for some users. Initially, around 14,000 user accounts were accessed through the credential stuffing campaign, which was then leveraged to breach the personal data of 6.9 million users participating in 23andMe’s DNA Relatives feature.
In a letter dated December 11, 2023, 23andMe contended that the victims themselves chose to share their information with others by opting into the DNA Relatives feature. The company further argued that the accessed information lacked critical data, such as social security numbers, driver’s license numbers, or payment details, minimizing the potential for “pecuniary harm.”
In response to the lawsuit filed by Bacus v 23andMe, Inc., which alleges the company’s failure to implement adequate security measures, 23andMe confirmed the implementation of additional security measures post-incident. These measures include ending all active logged-in user sessions, mandating password resets for all accounts, and requiring two-factor authentication for all customers.
However, industry experts have criticized 23andMe’s stance, asserting that the blame cannot be solely placed on users. Cybersecurity expert Erfan Shadabi emphasized the company’s duty to protect entrusted information and suggested that attributing blame entirely to users oversimplifies the complex landscape of cybersecurity. Nick Rago, Field CTO at Salt Security, challenged 23andMe’s assertion that the breach posed no financial harm, highlighting the potential consequences of exposing genealogy and relationship information in targeted social engineering campaigns. Rago pointed out recent breaches affecting other companies as examples of the effectiveness of such attacks in today’s cybersecurity environment.
-
FBI Expands Cybercrime Enforcement with Global Agent Deployment

The FBI is amplifying its efforts to combat cyber-related crime on an international scale by increasing the deployment of agents to American embassies abroad. This initiative marks a significant expansion, with six new positions, representing a nearly 40% increase in the FBI’s cyber assistant legal attachés (ALATs). The information reveals that new postings will be established in New Delhi, Rome, and Brasilia, bringing the total number of cyber-focused FBI agents deployed to U.S. embassies to 22.
The rise of cyber criminal operations, facilitated by global digital infrastructure, has created challenges for law enforcement due to the involvement of victims and perpetrators in diverse locations. Coordinating investigations and collecting time-sensitive evidence has become increasingly complex for domestic agencies.
Brian Abellera, the FBI’s cyber assistant legal attaché in Ottawa, emphasized the global nature of cybercrime, stating, “Their playing field, if you will, is the world.” Cyber assistant legal attachés are part of the larger legal attaché program, established in the early 1940s, providing a mechanism for law enforcement and intelligence agencies to collaborate internationally. The FBI currently operates 63 legal attaché offices in embassies and consulates covering more than 180 countries.
The FBI initiated the placement of cyber-focused agents in U.S. embassies in 2011, extending their presence to countries such as Romania, Australia, the Netherlands, Estonia, Ukraine, and Canada. This expansion aligns with a broader strategic shift by the FBI and the Department of Justice toward a proactive approach in combating cybercrime operations and infrastructure. The emphasis is on disrupting criminal groups’ activities rather than investigating incidents post facto.
U.S. Deputy Attorney General Lisa Monaco acknowledged this shift, stating that disrupting criminal operations is now a priority. Despite resulting in fewer arrests, this approach has proven effective in obtaining decryption keys, preventing ransomware payments, and dismantling cybercriminal networks.
A notable example is the April 2023 operation targeting the Genesis Market, a significant online services access credential marketplace. Coordinated by cyber legal attachés, the operation involved 17 countries, leading to 119 arrests, 208 property searches, and 97 “knock and talk measures.” The collaborative effort across multiple countries and time zones demonstrated the effectiveness of a unified approach.
Brian Abellera stressed the importance of international partnerships, emphasizing that the FBI alone lacks the resources, expertise, and reach to impose significant risks on adversaries. Looking ahead, Abellera is dedicated to combating international ransomware operations, emphasizing the vital role of trust and cooperation with international partners in maximizing impact on adversaries.
-
Syrian Hackers Unleash Destructive SilverRAT Trojan

The creators of a highly advanced remote access Trojan known as SilverRAT have established connections to both Turkey and Syria and are gearing up to launch an updated version of their tool. The current iteration, SilverRAT v1, functions exclusively on Windows systems, offering capabilities for constructing malware tailored for keylogging and ransomware attacks. Cyfirma, a Singapore-based cybersecurity firm, released a threat analysis on January 3, outlining SilverRAT’s destructive features, such as the ability to delete system restore points.
Cyfirma’s analysis emphasizes the increasing sophistication of cybercriminal groups in the region, underscoring the evolving nature of the underground markets. The first version of SilverRAT surfaced in October when its source code was leaked by unidentified actors. The leaked code comprised a builder enabling users to create a remote access Trojan with specific functionalities.
Noteworthy features identified by Cyfirma include the Trojan’s capacity to utilize either an IP address or webpage for command and control, evasion techniques for antivirus software, the capability to erase system restore points, and delayed execution of payloads. Two threat actors, operating under the aliases “Dangerous silver” and “Monstermc,” are identified as the developers behind both SilverRAT and a preceding program, S500 RAT.
These hackers conduct their operations on platforms such as Telegram and various online forums, where they engage in the sale of malware-as-a-service, distribute cracked RATs from other developers, and offer a range of related services. The group, known as Anonymous Arabic, maintains a blog and website. Rajhans Patel, a threat researcher with Cyfirma, has mentioned, “There are two people managing SilverRAT.

The dashboard designed for crafting trojans in SilverRAT. Source: Cyfirma.
The Anonymous Arabic group is active on forums such as Turkhackteam, 1877, and at least one Russian forum. In addition to developing SilverRAT, the group provides distributed denial-of-service (DDoS) attacks on demand through a botnet named “BossNet,” as observed since late November 2023.
While state-sponsored hacking groups from Iran and Israel have traditionally dominated the Middle East’s threat landscape, indigenous groups like Anonymous Arabic continue to thrive in the cybercrime markets. The ongoing evolution of tools like SilverRAT underscores the dynamic nature of the underground markets in the region.
The members of Anonymous Arabic exhibit diverse backgrounds, with at least one identified as a former game hacker in his early 20s residing in Damascus, Syria. Data gathered by Cyfirma researchers from the hacker’s Facebook profile, YouTube channel, and social media posts reveal a history of hacking activities initiated during his teenage years.
Cyfirma notes a growing trend where young hackers start their careers by exploiting games or launching denial-of-service attacks against gaming systems. The U.S. Department of Homeland Security’s Cyber Safety Review Board (CSRB) has identified the transition from juvenile hackers to cybercriminal enterprises as a significant threat. The CSRB recommends comprehensive programs to divert juveniles away from cybercrime, as illustrated by the success of groups like Lapsus$ in attacking well-resourced companies.
However, the allure of cybercrime persists for young programmers and technology-savvy teenagers. Sarah Jones, a cyber threat intelligence research analyst at Critical Start, emphasizes the diversity within hacker communities, acknowledging that some hackers may progress from game hacks to more serious tools and techniques. Despite efforts to redirect juveniles, cybercriminals often target industries and countries with weaker cyber defenses.
-
Cybersecurity Breach Hits West Virginia City, Exposing Sensitive Data

On Thursday, the city of Beckley, West Virginia, revealed that it is currently grappling with a cyberattack, as conveyed through a notice shared on social media. City authorities acknowledged the discovery of issues within their computer network and extended apologies for any inconveniences caused.
In their statement, officials expressed their commitment to diligently investigate the incident’s source, ascertain its complete scope and impact, and determine the potential compromise of data. While urging individuals with questions to reach out, they refrained from commenting on whether the cyber incident involved ransomware or if the perpetrating group had claimed responsibility.
Situated approximately 50 minutes from the Virginia border, Beckley boasts a population exceeding 17,000 and serves as the central hub for the Beckley metropolitan area, housing around 115,000 residents. Beckley Mayor Rob Rappold confirmed the cyberattack in an interview with a local news station but was unable to provide a timeline for the restoration of affected systems.
This latest incident follows a trend of cyberattacks targeting small governments across the United States throughout 2023. In a notable case last February, nearly 20,000 students in another region of West Virginia faced disruptions in their classes due to a cyberattack on their school.
Cybersecurity firm Emsisoft reported tracking attacks on at least 95 government entities in 2023, with headline-grabbing incidents affecting cities such as Oakland and Dallas.
Adding to the string of cyber challenges, the city of Huber Heights in Ohio disclosed this week that it is still grappling with the aftermath of a ransomware attack experienced in November. According to reports from the Dayton Daily News, the city remains under a state of emergency due to the impact of the attack. The city council approved $350,000 in funds to address the incident, covering expenses for a response and recovery cybersecurity firm, ransomware negotiators, as well as new devices and updated systems for city operations.
City Manager Rick Dzik, cautious not to speculate on potential data releases, emphasized the risk to a broad range of information stored on city servers and computers, from routine documents to personal data. The primary challenge remains in determining definitively what kind of data may have been compromised.
Inicio
1 minute