Abdali Hospital, situated in the modern Al-Abdali development of Amman, Jordan, is a comprehensive medical facility offering a range of specialized services. The hospital caters to diverse medical needs, encompassing general surgery, orthopedics, rheumatology, gynecology, urology, endocrinology, neurology, nephrology, pulmonology, internal medicine, oncology, infectious disease, and anesthesiology. Additionally, Abdali Hospital features aesthetic specialties, including plastic surgery and dermatology, along with a dedicated women’s health center specializing in breast cancer care.
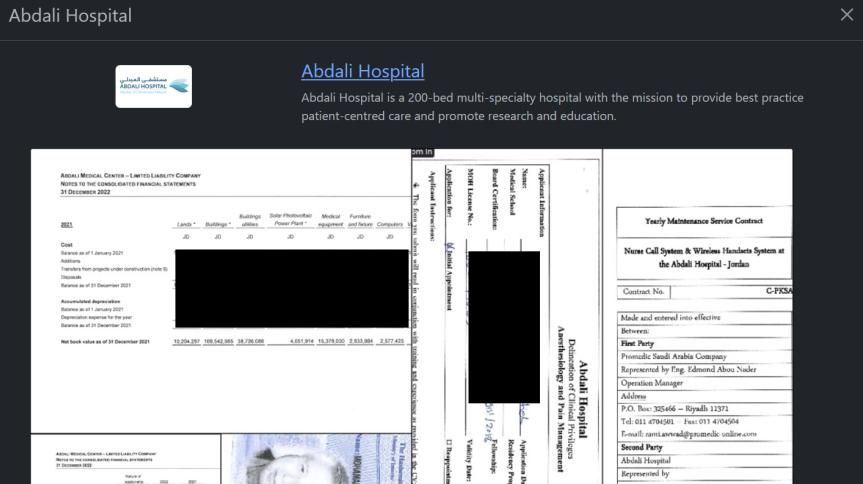
Recent reports indicate that the Rhysida ransomware group has claimed responsibility for breaching Abdali Hospital in Jordan, adding it to their list of victims on their Tor leak site. The group has purportedly published images of stolen documents, including ID cards and contracts, as evidence of the successful hack.
A message posted on the Tor leak site of the Rhysida ransomware group declares, “Act within the next 7 days to bid on exceptional, distinct, and noteworthy data. Prepare to open your wallets and secure the purchase of exclusive data. Our sales are exclusive to one party, strictly prohibiting any resale. You will be the sole owner of the acquired information!”
The ransomware operators claim to have acquired a significant amount of ‘sensitive data’ and are auctioning it for 10 BTC. Notably, the group intends to sell the stolen data to a single buyer and plans to publicly release the data over a seven-day period.
Rhysida ransomware has been active since May 2023, with at least 62 companies identified as victims of their operations, spanning various industries, including education, healthcare, manufacturing, information technology, and government sectors. The group targets “targets of opportunity” and has recently claimed responsibility for attacks on King Edward VII’s Hospital in London, the British Library, and the China Energy Engineering Corporation.
In response to the growing threat, the FBI and CISA issued a joint Cybersecurity Advisory (CSA) as part of the ongoing #StopRansomware effort. The advisory warns of Rhysida ransomware attacks and includes information on tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with the group. The report highlights the group’s use of external-facing remote services, exploitation of Zerologon (CVE-2020-1472), and reliance on living off-the-land techniques using native network administration tools for malicious operations.





Leave a comment