Elevation of privilege vulnerabilities represents the prevailing weakness exploited by internal personnel engaged in unauthorized activities within corporate networks, either for malicious intentions or by recklessly acquiring and utilizing risky tools.
A report from Crowdstrike, analyzing data spanning from January 2021 to April 2023, underscores a surge in insider threats, with a significant proportion involving the exploitation of privilege escalation vulnerabilities.
According to the report, 55% of the recorded insider threats hinge on privilege escalation exploits, while the remaining 45% involve unwittingly introducing risks through the download or misuse of offensive tools.
Typically, rogue insiders turn against their employers due to financial incentives, personal animosity, or disagreements with supervisors. Crowdstrike broadens the scope of incidents categorized as insider threats to include activities such as utilizing exploits to install software or conducting security testing, even if not inherently malicious.
The financial repercussions of insider threats are substantial, with attacks originating from within organizations costing an average of $648,000 for malicious incidents and $485,000 for non-malicious ones. These figures are expected to rise in 2023.
Beyond the direct financial impact, Crowdstrike emphasizes the indirect consequences, including damage to brand and reputation.
Privilege escalation vulnerabilities are crucial for many insider attacks, as malicious actors often begin with low-level access to network environments. Elevated privileges enable attackers to perform actions like downloading unauthorized software, wiping logs, or diagnosing computer problems using tools requiring administrator privileges.
CrowdStrike identifies several frequently exploited flaws for local privilege escalation by rogue insiders, including CVE-2017-0213, CVE-2022-0847 (DirtyPipe), CVE-2021-4034 (PwnKit), CVE-2019-13272, CVE-2015-1701, and CVE-2014-4113. These flaws, listed in CISA’s Known Exploited Vulnerabilities Catalog, have historical associations with attacks by threat actors.
Even if systems are patched for these flaws, insiders can still gain elevated privileges through other means, such as DLL hijacking flaws, insecure file system permissions, or Bring Your Own Vulnerable Driver (BYOVD) attacks.
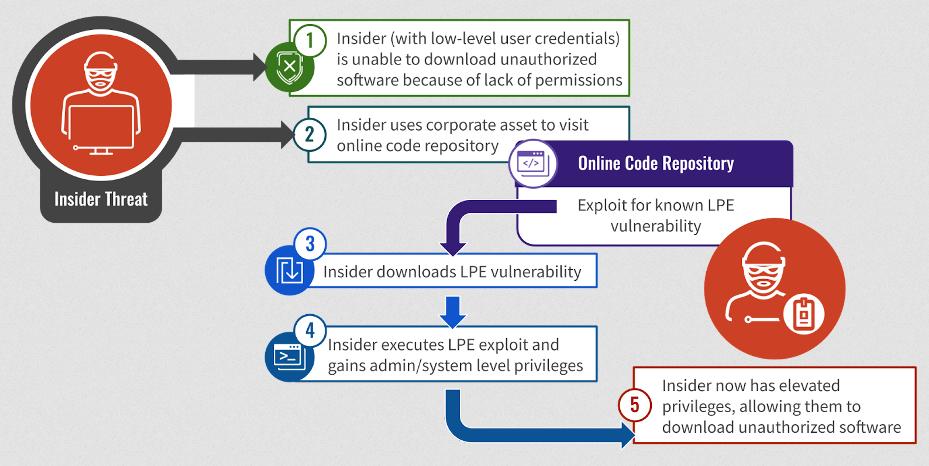
Diagram of an insider attack. Source: CrowdStrike
Crowdstrike provides examples of real-world exploits, such as an employee downloading an exploit via WhatsApp to install uTorrent and play games, or an attempt to gain administrative rights for troubleshooting by exploiting PwnKit.
While many insider incidents may not be inherently malicious, they introduce risks by altering device functionality or potentially running insecure programs on the network.
Nearly half of the recorded insider incidents involve unintentional mistakes, including exploit testing going awry, executing offensive security tools without proper safeguards, and downloading unvetted code. These incidents often result from security professionals testing exploits on production workstations rather than through segmented virtual machines.
The introduction of vulnerabilities like CVE-2021-42013, CVE-2021-4034 (PwnKit), CVE-2020-0601, CVE-2016-3309, and CVE-2022-21999 into corporate networks raises the overall security risk, providing additional vectors for exploitation by threat actors already present in the network.
Furthermore, threat actors may create fake proof-of-concept exploits or security tools that install malware on devices, amplifying the potential for cyber espionage, data theft, or ransomware attacks. Recent instances have demonstrated the distribution of fake exploits leading to the installation of backdoors and malware on corporate networks.





Leave a comment