Security experts are sounding the alarm about the exposure of Kubernetes configuration secrets, raising concerns about potential vulnerabilities to supply chain attacks.
A recent report by Aqua security researchers, Yakir Kadkoda and Assaf Morag, highlights the risk posed by publicly accessible Kubernetes configuration secrets. These secrets, encoded and uploaded to public repositories, have caught the attention of cybersecurity researchers, who identified two leading blockchain companies and various Fortune 500 firms among the affected organizations.
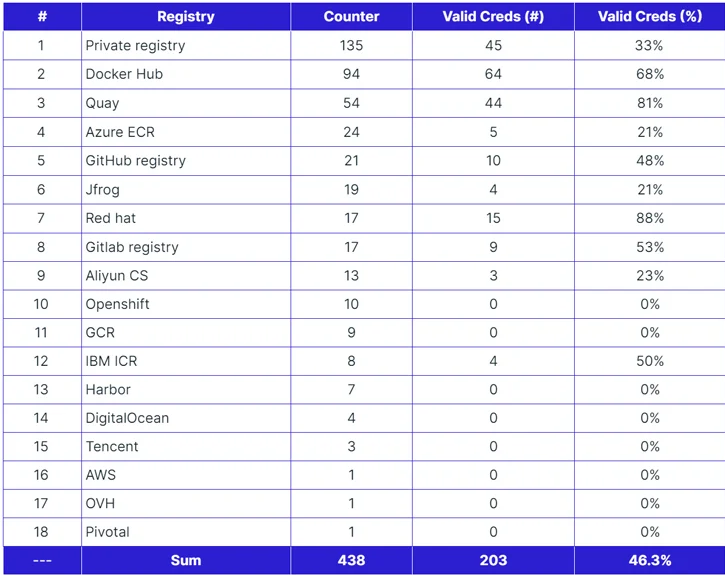
Utilizing the GitHub API to retrieve entries containing .dockerconfigjson and .dockercfg types—repositories storing credentials for accessing container image registries—the researchers uncovered 438 records potentially containing valid credentials. Alarmingly, 46% of these records, totaling 203, provided access to the respective registries.
Of these credentials, 93 passwords were manually set by individuals, while 345 were computer-generated. Notably, the majority of these credentials granted both pulling and pushing privileges, exposing private container images within the registries.
Worryingly, almost half of the manually set passwords were identified as weak, including commonly insecure choices like “password,” “test123456,” “windows12,” “ChangeMe,” and “dockerhub.” The researchers emphasized the urgent need for robust organizational password policies to deter the use of such vulnerable passwords.
Aqua also noted instances where organizations neglected to remove secrets from files committed to public GitHub repositories, unintentionally exposing sensitive information.
However, there were positive findings as well. Credentials associated with AWS and Google Container Registry (GCR) were temporary and expired, preventing unauthorized access. Additionally, the GitHub Container Registry implemented two-factor authentication (2FA) as an extra layer of protection.
The researchers highlighted variations in the security of exposed keys, noting that some were encrypted, limiting their utility. In other cases, valid keys had minimal privileges, typically restricted to pulling or downloading specific artifacts or images.
The report underscores the broader challenges identified in Red Hat’s State of Kubernetes Security Report earlier this year, emphasizing vulnerabilities and misconfigurations as top concerns in container environments. Of the 600 respondents surveyed, 37% identified revenue or customer loss resulting from container and Kubernetes security incidents.





Leave a comment