North Korean threat actors have been linked to two campaigns where they assume the roles of job recruiters and seekers to disseminate malware and illicitly secure employment with organizations across the U.S. and other global regions.
Palo Alto Networks Unit 42 has designated these malicious endeavors as Contagious Interview and Wagemole, respectively. The former focuses on infecting software developers with malware under the guise of a fabricated job interview, while the latter is geared towards financial gain and espionage.
The primary objective of the Contagious Interview campaign is believed to be cryptocurrency theft, utilizing compromised targets as a staging ground for subsequent attacks, according to the cybersecurity company.
In the deceptive job-seeking activity, a GitHub repository is employed to host resumes featuring forged identities that impersonate individuals of various nationalities.
The Contagious Interview attacks introduce two previously undocumented cross-platform malware named BeaverTail and InvisibleFerret. These malware strains are capable of running on Windows, Linux, and macOS systems.
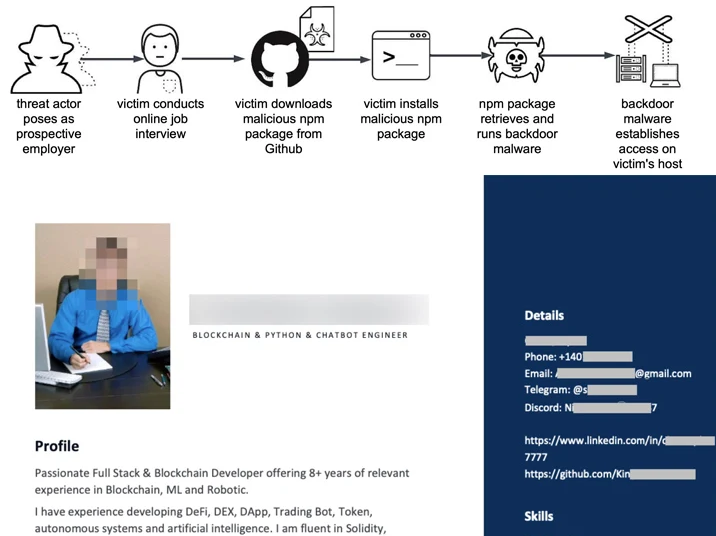
Notably, this intrusion set shares tactical similarities with the previously reported North Korean threat activity known as Operation Dream Job. This operation involves approaching employees with false job offers, tricking them into downloading a malicious npm package hosted on GitHub as part of a simulated online interview.
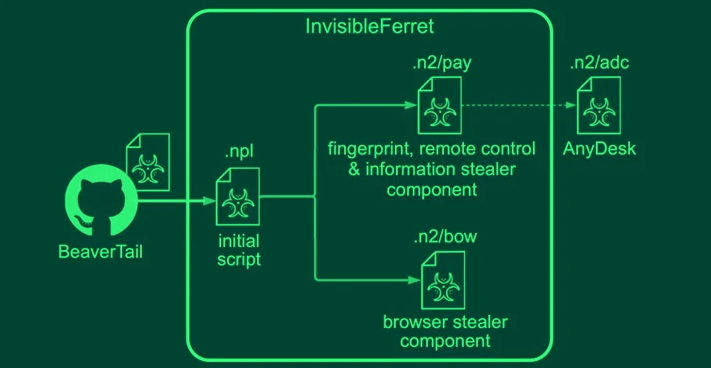
BeaverTail, the JavaScript implant, functions as a stealer and loader with the ability to pilfer sensitive information from web browsers and cryptocurrency wallets. It can also deliver additional payloads, including InvisibleFerret, a Python-based backdoor featuring fingerprinting, remote control, keylogging, and data exfiltration capabilities.
InvisibleFerret is designed to download the AnyDesk client from a server controlled by the threat actor, enabling remote access.
Recently, Microsoft warned about the Lazarus Group sub-cluster Sapphire Sleet (aka BlueNoroff) establishing new infrastructure that impersonates skills assessment portals in their social engineering campaigns.
This is not the first instance of North Korean threat actors exploiting fake modules in npm and PyPI. In June and July 2023, Phylum and GitHub detailed a social engineering campaign targeting personal accounts of technology firm employees, aiming to install a counterfeit npm package under the guise of collaborating on a GitHub project.
The discovery of Wagemole aligns with a U.S. government advisory revealing North Korea’s subterfuge to evade sanctions by deploying highly skilled IT workers globally, channeling their wages back to fund the country’s weapons programs.
The campaigns involve resumes with links to LinkedIn profiles and GitHub content, with these GitHub accounts appearing well-maintained and indistinguishable from legitimate ones, showcasing frequent code updates and engagement with other developers.
In a revealing statement to Reuters, a defected North Korean IT worker disclosed, “We would create 20 to 50 fake profiles a year until we were hired.”
This development occurs as North Korea claims success in launching a military spy satellite into space, following two unsuccessful attempts earlier in the year. Additionally, it follows a fresh attack campaign by the North Korea-linked Andariel group, a Lazarus subordinate, deploying various RATs via infiltrating vulnerable MS-SQL servers and supply chain attacks using South Korean asset management software.
Unit 42 warns of the persistent threat posed by Contagious Interview, especially targeting software developers who often constitute a vulnerable link in supply chain attacks. Wagemole, on the other hand, represents an opportunity for threat actors to embed insiders within targeted companies.





Leave a comment