Phishing campaigns distributing malware families such as DarkGate and PikaBot are employing tactics reminiscent of previous attacks associated with the now-defunct QakBot trojan.
Cofense, in a report noted, “These include hijacked email threads as the initial infection, URLs featuring distinctive patterns that restrict user access, coupled with an infection chain closely mirroring the QakBot delivery process. The employed malware families also align with the expectations for use by QakBot affiliates.”
QakBot, also known as QBot and Pinkslipbot, was dismantled in August as part of a coordinated law enforcement effort called Operation Duck Hunt.
The choice of DarkGate and PikaBot in these campaigns is unsurprising, given their ability to serve as conduits for delivering additional payloads to compromised hosts, making them appealing to cybercriminals.
Zscaler had previously highlighted PikaBot’s similarities to QakBot in its May 2023 analysis, citing parallels in “distribution methods, campaigns, and malware behaviors.”
DarkGate, on the other hand, employs advanced techniques to elude detection by antivirus systems. It possesses capabilities such as logging keystrokes, executing PowerShell, and implementing a reverse shell, enabling operators to take control of an infected host remotely.
Sekoia, in a recent technical report, stated, “The link is two-way, allowing attackers to both send commands and receive real-time responses. This capability empowers them to maneuver through the victim’s system, extract data, and execute various malicious actions.”
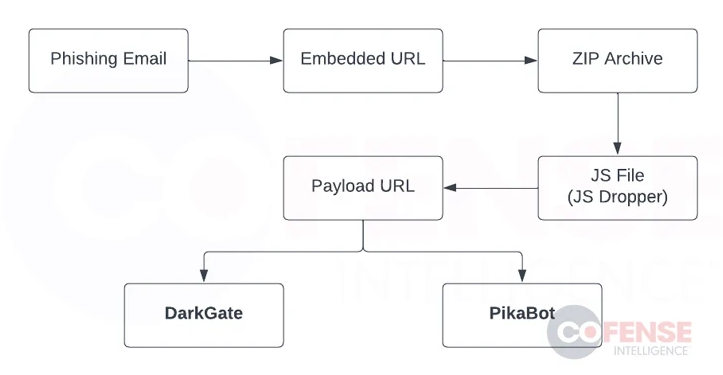
Cofense’s analysis of the high-volume phishing campaign reveals its broad targeting across various sectors. The attack chains involve a booby-trapped URL within hijacked email threads, directing users to a ZIP archive. Within the archive, a JavaScript dropper is found, contacting a second URL to download and execute either the DarkGate or PikaBot malware.
A notable variant of these attacks observed the use of Excel add-in (XLL) files instead of JavaScript droppers to deliver the final payloads.
Cofense emphasized that a successful DarkGate or PikaBot infection could result in the deployment of advanced crypto mining software, reconnaissance tools, ransomware, or any other malicious file chosen by threat actors for installation on the victim’s machine.





Leave a comment