A group of academic researchers hailing from universities in California and Massachusetts recently demonstrated the potential vulnerability of SSH (secure shell) connections under specific conditions. The researchers discovered that passive network attackers could potentially extract secret RSA keys from errors occurring during failed SSH connection attempts.
SSH serves as a cryptographic network protocol widely utilized for secure communication, remote system access, file transfers, and system administration tasks. RSA, a public-key cryptosystem integral to SSH for user authentication, relies on a private key to decrypt communication encrypted with a public, shareable key.
The research paper, authored by Keegan Ryan, Kaiwen He, Nadia Heninger, and George Arnold Sullivan, details the feasibility of passive network attackers obtaining a private RSA key from SSH servers experiencing faults in signature computation. The RSA algorithm utilizes the Chinese Remainder Theorem (CRT) to decrease the bit size of the public key and improve the speed of decryption.
The researchers explained that these attacks exploit errors in computing modulo one prime, such that if a fault occurs during the computation, an invalid signature is generated, making it equivalent to the correct signature modulo one prime factor but not another. While such errors are infrequent, they are inevitable due to hardware flaws, allowing attackers to exploit numerous opportunities given a sufficiently large dataset.
Previously thought to be immune to this type of attack, SSH was proven vulnerable by the researchers using lattice-based attacks to recover private keys from partially known nonces. Despite their tests not covering RSA-1024, SHA512, the researchers asserted the efficiency of the lattice attack, achieving a 100% success rate.
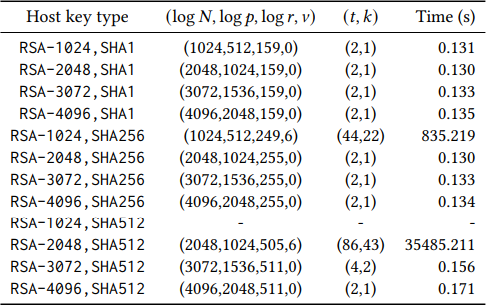
Secret key recovery times on Intel Xeon E5-2699. Source: eprint.iacr.org
Through their lattice attack, the researchers identified 4,962 invalid signatures, exposing the factorization of corresponding RSA public keys and enabling the retrieval of private keys for 189 unique RSA public keys. Notably, many of the compromised secrets originated from devices with vulnerable implementations, with the highest number of compromised signatures linked to Zyxel devices.
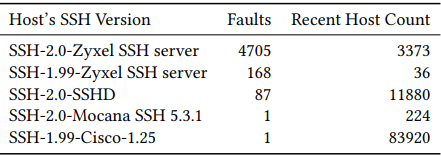
Devices matching the generated signatures. Source: eprint.iacr.org
Upon discovering the issue, the researchers promptly alerted Cisco and Zyxel. Cisco, having implemented a suitable mitigation in ASA and FTD Software the previous year, assured ongoing efforts to address mitigations in IOS and IOS XE Software. Zyxel, on the other hand, identified that the ZLD firmware version used in the experiment had transitioned to OpenSSL, eliminating the identified risk.
The researchers emphasized the need for implementations that validate signatures before transmission as a countermeasure against attackers retrieving secret keys. They recommended tools like the OpenSSH suite, which relies on OpenSSL for signature generation, to enhance security in SSH connections.





Leave a comment