Following the Sandworm and APT28 cyber threats, another state-sponsored Russian hacking group, APT29, also known as UNC3524, NobleBaron, Dark Halo, NOBELIUM, Cozy Bear, CozyDuke, and SolarStorm, is exploiting the CVE-2023-38831 vulnerability within WinRAR for its cyber operations.
This security flaw impacts WinRAR versions preceding 6.23, allowing the creation of .RAR and .ZIP archives that can execute background code, prepared by attackers for malicious purposes.
Since April, threat actors targeting cryptocurrency and stock trading forums have been exploiting CVE-2023-38831 as a zero-day vulnerability. A recent report from the Ukrainian National Security and Defense Council (NDSC) reveals that APT29 is using a malicious ZIP archive named “DIPLOMATIC-CAR-FOR-SALE-BMW.pdf.” This archive runs a script in the background, displaying a PDF lure and downloading PowerShell code to execute a payload.
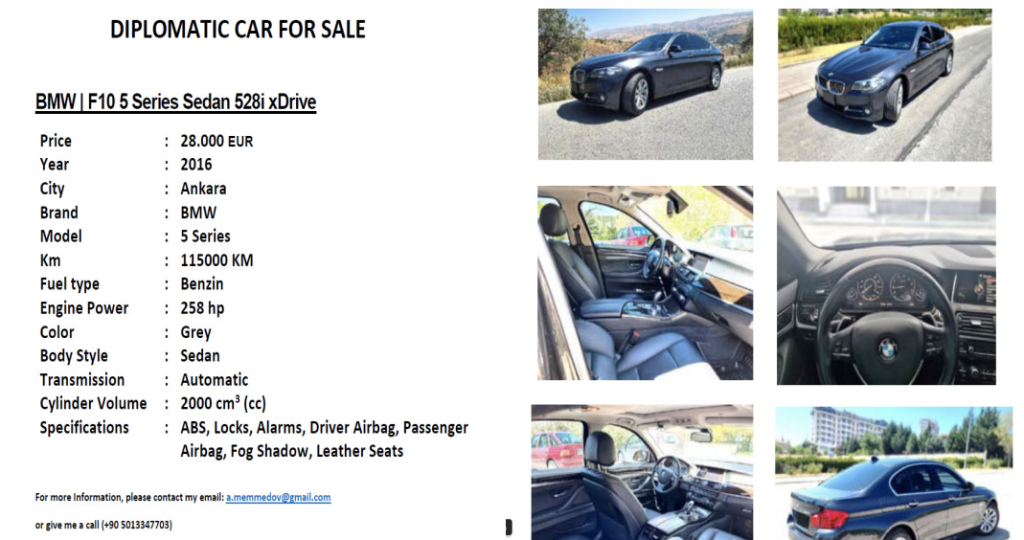
The cyber attacks by APT29 have targeted multiple European countries, including Azerbaijan, Greece, Romania, and Italy, with a lure involving a BMW car sale. APT29 previously employed this BMW car ad phishing lure in May during a campaign in Ukraine, utilizing ISO payloads via the HTML smuggling technique.
In the recent attacks, APT29 combined the old phishing tactic with a new technique, using a Ngrok free static domain (a feature announced by Ngrok on August 16) to reach the command and control (C2) server hosted on their Ngrok setup. This method allowed the hackers to conceal their activities and communicate with compromised systems without the risk of detection.
Since the disclosure of the CVE-2023-38831 vulnerability by cybersecurity company Group-IB, advanced threat actors have integrated it into their attacks. In August, security researchers at ESET observed APT28 exploiting the vulnerability in a spear-phishing campaign targeting political entities in the EU and Ukraine, using the European Parliament agenda as a lure.
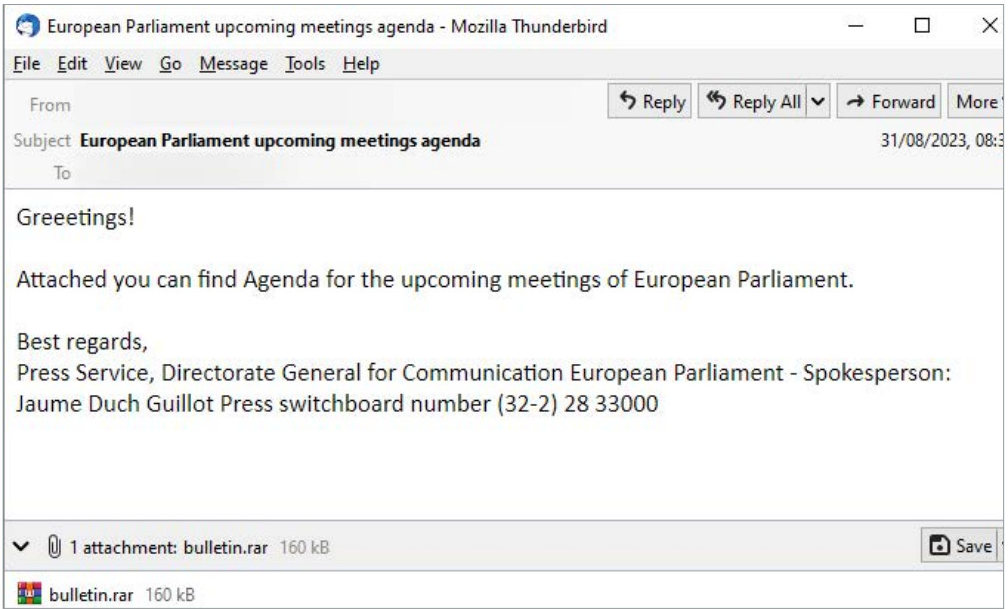
A Google report in October highlighted that Russian and Chinese state hackers exploited the security issue to steal credentials and sensitive data, establishing persistence on target systems.
The Ukrainian NDSC notes that APT29’s campaign is noteworthy for blending old and new techniques, incorporating the WinRAR vulnerability for payload delivery and Ngrok services to conceal communication with the C2. The agency’s report provides indicators of compromise (IoCs), including filenames, hashes for PowerShell scripts and email files, as well as domains and email addresses.





Leave a comment