Apple’s “Find My” location network has the potential for misuse, allowing malicious actors to discreetly transmit sensitive information gathered by keyloggers installed in keyboards.
The Find My network and its associated application serve the primary purpose of aiding users in locating misplaced or lost Apple devices, such as iPhones, iPads, Macs, Apple Watches, AirPods, and Apple Tags.
This service operates by harnessing GPS and Bluetooth data sourced from countless Apple devices across the globe, enabling the tracking of devices reported as lost or stolen, even if they are offline.
When a lost device emits Bluetooth signals in a continuous loop, nearby Apple devices pick up these signals and anonymously relay the device’s location to the owner via the Find My network.
The potential for misusing Find My to transmit data beyond device location was initially discovered by Positive Security researchers, led by Fabian Bräunlein and his team, more than two years ago. It appears that Apple has since taken steps to address this issue.
The researchers have even shared their implementation on GitHub, which they’ve aptly named ‘Send My.’ This tool allows others to leverage the Find My network for uploading arbitrary data and retrieving it from any internet-enabled device worldwide.
As initially reported by Heise, the researchers created a proof-of-concept hardware device to underscore the potential risks associated with this misuse. They integrated a keylogger with an ESP32 Bluetooth transmitter into a USB keyboard to demonstrate that it is feasible to relay passwords and other sensitive data typed on the keyboard through the Find My network using Bluetooth technology.
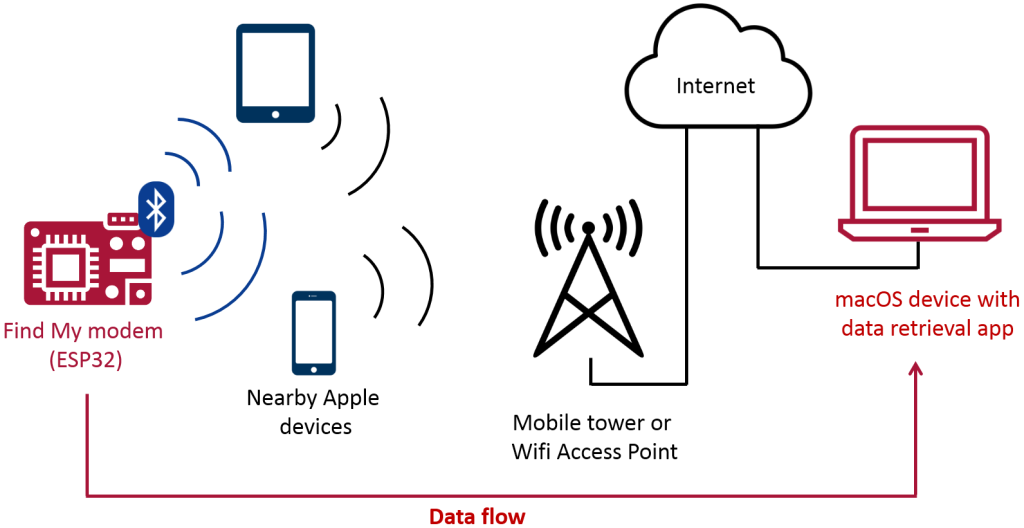
Generic attack diagram. Source: Positive Security
Bluetooth transmission offers a higher level of stealth compared to WLAN keyloggers or Raspberry Pi devices, which may stand out in well-secured settings. The Find My platform has the unique capability to discreetly utilize ubiquitous Apple devices for data relay.
Notably, the keylogger does not necessarily require an AirTag or an officially supported chip. This is because Apple devices are programmed to respond to any Bluetooth message. If the message is correctly formatted, the receiving Apple device will generate a location report and seamlessly transmit it to the Find My network.
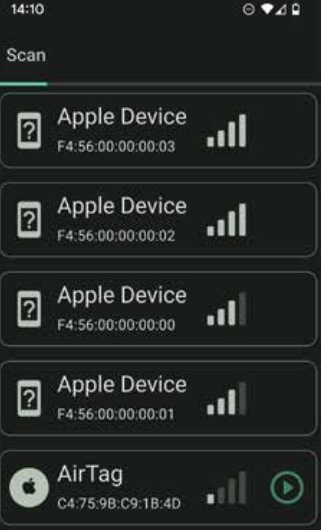
Unknown Apple device entries. Source: Heise
The sender must generate numerous subtly varied public encryption keys, mimicking multiple AirTags, and insert arbitrary data into these keys by allocating specific bits at predefined locations within them.
In this manner, the numerous reports fetched from the cloud can be merged and deciphered at the receiving end to access the arbitrary data, specifically the keylogger’s captured information.
Bräunlein detailed that the overall cost of this data-extraction setup was approximately $50, comprising a Bluetooth-enabled variant of the ‘EvilCrow’ keylogger and a standard USB keyboard.
The proof-of-concept attack achieved a transmission rate of 26 characters per second and a reception rate of 7 characters per second, with a latency ranging from 1 to 60 minutes, contingent on the presence of Apple devices within the keylogger’s range.
While the speed might not be exceptionally rapid, if the objective is to retrieve valuable information like passwords, waiting several hours or even days would not deter malicious actors.
The noteworthy aspect is that Apple’s anti-tracking safeguards that alert users to potential AirTag tracking do not activate when dealing with the stationary keylogger concealed within the keyboard, ensuring the device remains concealed and less likely to be uncovered.





Leave a comment