The Iranian state-sponsored cyber group, known as MuddyWater, has been identified as the culprit behind a fresh spear-phishing campaign aimed at two Israeli entities. The primary objective of this operation was to deploy the legitimate remote administration tool, Advanced Monitoring Agent, from N-able.
Cybersecurity firm Deep Instinct, which brought this campaign to light, has stated that it displays “updated Tactics, Techniques, and Procedures (TTPs)” compared to MuddyWater’s previous activities. In the past, MuddyWater employed similar attack chains to disseminate various remote access tools, such as ScreenConnect, RemoteUtilities, Syncro, and SimpleHelp.
While this incident marks the first instance of MuddyWater using N-able’s remote monitoring software, it also highlights the fact that their modus operandi, although largely unchanged, continues to achieve some level of success for the threat actor.
These findings have been independently verified by cybersecurity company Group-IB in a post shared on social media.
MuddyWater is a state-sponsored group engaged in cyber espionage, operating as a subordinate element within Iran’s Ministry of Intelligence and Security (MOIS). It joins other MOIS-affiliated clusters, such as OilRig, Lyceum, Agrius, and Scarred Manticore, and has been active since at least 2017.
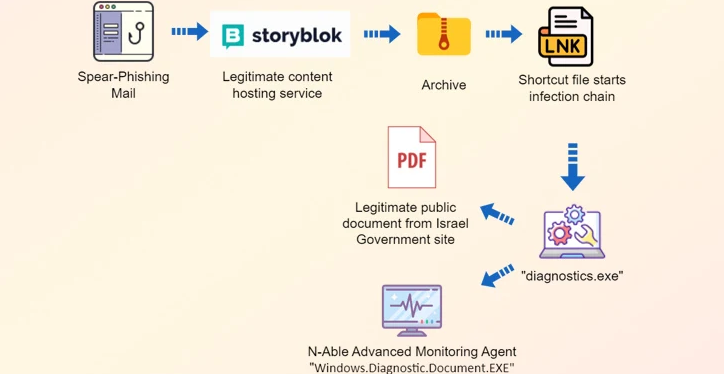
Previous attack strategies involved sending spear-phishing emails with direct links and various file attachments (HTML, PDF, and RTF) containing links to archives hosted on file-sharing platforms. These archives would ultimately deploy one of the remote administration tools mentioned earlier.
The latest tactics and tools represent a combination of continuity and evolution for the group, which is also known as Mango Sandstorm and Static Kitten.
What sets this campaign apart is the utilization of a new file-sharing service called Storyblok to initiate a multi-stage infection process. It involves hidden files, an LNK file to trigger the infection, and an executable file to unhide a decoy document while deploying Advanced Monitoring Agent, a remote administration tool. After infecting the victim, MuddyWater operators use this legitimate remote administration tool to conduct reconnaissance on the target.
The lure document presented to the victim is an official memo from the Israeli Civil Service Commission, which can be publicly downloaded from its official website.
In a sign of Iran’s advancing cyber capabilities, Deep Instinct also discovered MuddyWater actors employing a new command-and-control (C2) framework known as MuddyC2Go, succeeding MuddyC3 and PhonyC2.





Leave a comment