The Pwn2Own Toronto 2023 hacking competition has concluded, with security researchers securing a total of $1,038,500 for their successful exploits, which included 58 zero-day vulnerabilities and multiple instances of bug collisions. This competition took place from October 24 to October 27 and was organized by Trend Micro’s Zero Day Initiative (ZDI), focusing on consumer products.
During the event, security researchers set their sights on a wide array of mobile and IoT devices. The range of targets included a variety of devices such as mobile phones (like the Apple iPhone 14, Google Pixel 7, Samsung Galaxy S23, and Xiaomi 13 Pro), in addition to printers, wireless routers, network-attached storage (NAS) devices, home automation hubs, surveillance systems, smart speakers, and Google’s Pixel Watch and Chromecast devices. Importantly, all these devices were in their default configurations and running the latest security updates.
Although no teams took up the challenge to hack the Apple iPhone 14 and Google Pixel 7 smartphones, the Samsung Galaxy S23 was a notable focus of attention. This fully patched device fell victim to successful exploits four times.
The Pentest Limited team led the charge, demonstrating a zero-day vulnerability in the Samsung Galaxy S23. They exploited an improper input validation weakness to gain code execution, reaping a reward of $50,000 and 5 Master of Pwn points. The STAR Labs SG team also capitalized on a permissive list of allowed inputs to hack the Samsung flagship, securing $25,000, with half the prize awarded for the second successful attempt on the same device, alongside 5 Master of Pwn points.
On the second day of the competition, security researchers from Interrupt Labs and the ToChim team joined the ranks of successful Galaxy S22 hackers, utilizing a permissive list of allowed inputs and another improper input validation weakness.
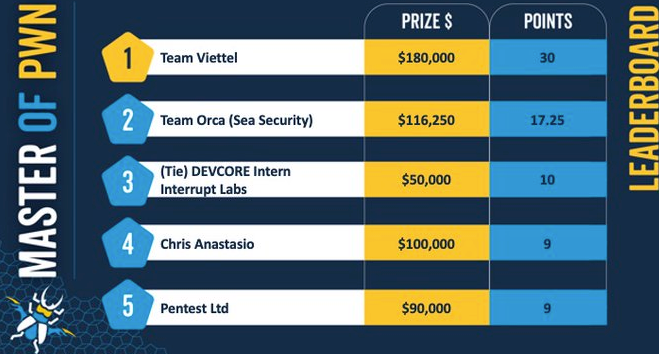
The top honors in the competition went to Team Viettel, who earned $180,000 and a total of 30 Master of Pwn points. They were followed by Team Orca of Sea Security, who secured $116,250 and 17.25 points. DEVCORE Intern and Interrupt Labs each pocketed $50,000 and gained 10 points.
In total, security researchers demonstrated successful exploits targeting 58 zero-day vulnerabilities across devices from various manufacturers, including Xiaomi, Western Digital, Synology, Canon, Lexmark, Sonos, TP-Link, QNAP, Wyze, Lexmark, and HP.
It is worth noting that vendors now have a 120-day window to release patches for the zero-day vulnerabilities exploited during the Pwn2Own event before ZDI discloses them publicly.
In March, during the Pwn2Own Vancouver 2023 competition, participants amassed $1,035,000 in rewards and even secured a Tesla Model 3 car by identifying 27 zero-day vulnerabilities and encountering several instances of bug collisions.





Leave a comment