In a coordinated international effort, law enforcement agencies have apprehended a malware developer associated with the Ragnar Locker ransomware group, and they’ve also taken control of the group’s dark web resources. The Ragnar Locker gang has been responsible for launching cyberattacks against 168 global companies since 2020.
The main figure behind this malevolent ransomware strain was arrested in Paris, France, on October 16th, with his residence in Czechia subsequently being searched. In the days that followed, five individuals were interviewed in Spain and Latvia as part of this operation, as confirmed by Europol.
At the culmination of this week-long action, the primary suspect, suspected of having a pivotal role within the Ragnar group, was presented before the examining magistrates of the Paris Judicial Court. Concurrently, Ukrainian law enforcement authorities carried out a raid on the premises of another alleged member of the gang in Kyiv. This operation led to the confiscation of laptops, mobile phones, and electronic devices.
Eurojust initiated the case in May 2021 following a request from French authorities. It facilitated five coordination meetings to enhance collaboration among the different law enforcement agencies involved in the investigation.
This collaborative effort united authorities from multiple countries, including Germany, Italy, Latvia, the Netherlands, France, the Czech Republic, Spain, Sweden, Japan, the United States and Canada. Notably, this marks the third such operation targeting the same ransomware gang.
The first of these operations occurred in September 2021, when coordinated efforts involving French, Ukrainian, and US authorities led to the arrest of two suspects in Ukraine. In October 2022, another suspect was detained in Canada through a joint operation conducted by French, Canadian, and US law enforcement agencies.
During this combined operation, law enforcement agents also seized cryptocurrency assets and dismantled Ragnar Locker’s Tor negotiation and data leak sites on a Thursday. Europol reported that nine servers were taken down, comprising five in the Netherlands, two in Germany, and two in Sweden.
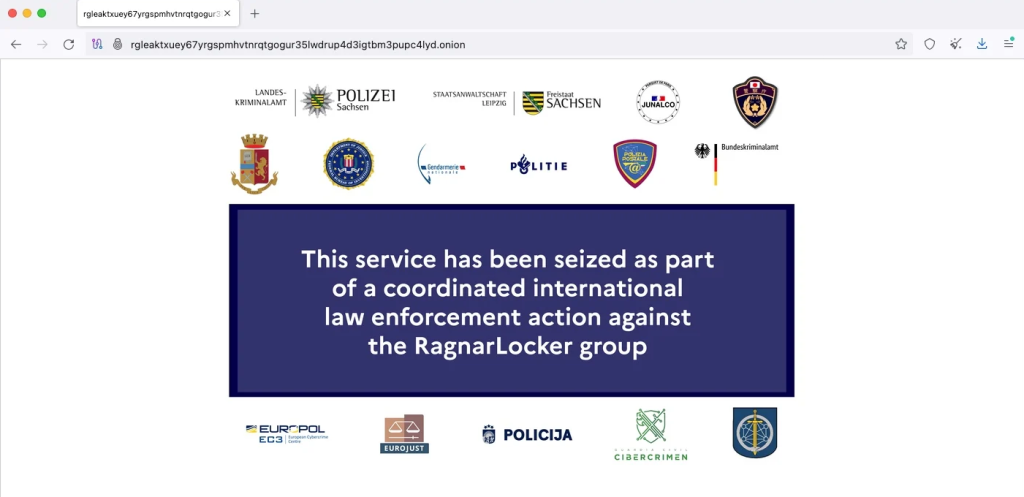
A message showcased on the data leak site of Ragnar Locker conveyed, “This service has been taken over in a joint law enforcement operation targeting the Ragnar Locker group.”
In a parallel development, the Ukrainian Cyber Alliance (UCA) successfully hacked the Trigona Ransomware operation. This resulted in the retrieval of data and the wiping of the cybercriminals’ servers.
Ragnar Locker, also known as Ragnar_Locker and RagnarLocker, first emerged in late December 2019, focusing its cyberattacks on enterprise targets worldwide. Unlike many contemporary ransomware gangs that operate using the Ransomware-as-a-Service model, recruiting affiliates to breach networks and deploy ransomware, Ragnar Locker had a unique approach. They operated semi-privately, eschewing active recruitment of affiliates and instead collaborating with external penetration testers to breach networks.
Their roster of past victims encompasses prominent names like ADATA, a computer chip manufacturer, the aviation heavyweight Dassault Falcon, and the Japanese gaming company Capcom. An FBI advisory issued in March 2022 disclosed that this ransomware had struck a minimum of 52 organizations spanning diverse critical infrastructure sectors in the United States since April 2020.





Leave a comment