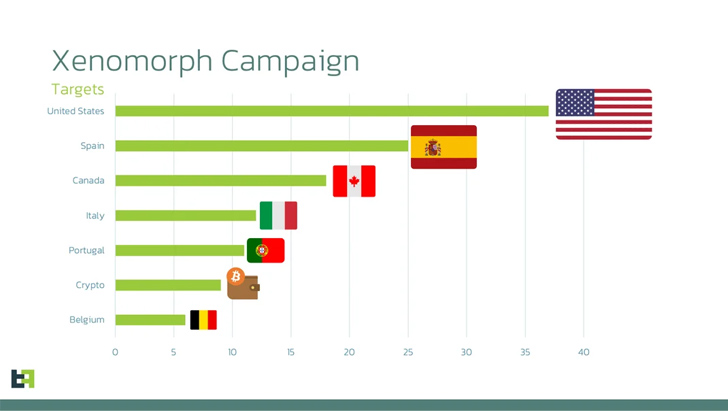
An enhanced variant of the Android banking trojan Xenomorph has surfaced, with its primary focus being over 35 financial institutions in the U.S. Dutch security firm ThreatFabric revealed that the campaign employs phishing web pages to entice victims into installing malicious Android apps. This new version targets a wider range of apps compared to its predecessors and extends its reach to several other countries including Spain, Italy, Canada, and Belgium.
The updated Xenomorph includes dozens of new overlays for institutions in the United States, Portugal, and various crypto wallets. This aligns with the trend observed in banking malware families over the past year, as stated in ThreatFabric’s analysis.
Xenomorph is a variant of the Alien banker malware, which initially appeared in 2022. The malware was distributed through a dropper called BugDrop, which bypassed security features in Android 13.
In a recent iteration identified in March, the malware incorporated the Automatic Transfer System (ATS) to carry out fraudulent activities. The ATS allows the operators, known as Hadoken Security, to gain complete control over the compromised device by leveraging Android’s accessibility privileges. This enables illicit fund transfers from the compromised device to an account controlled by the threat actors.
The malware utilizes overlay attacks to steal sensitive information, such as login credentials and credit card numbers, by displaying fake login screens on top of targeted banking apps. The overlays are obtained from a remote server in the form of a list of URLs.
The ATS framework automates the extraction of credentials, access to account balance information, transaction initiation, acquisition of MFA tokens from authenticator apps, and fund transfers, all without requiring human intervention.
The researchers noted that the malware developers have invested significant effort in modules that support Samsung and Xiaomi devices, which collectively represent around 50% of the Android market share.
The latest versions of Xenomorph introduce new features, including an “antisleep” function that prevents the phone’s screen from turning off by generating an active push notification. It also includes the ability to simulate a simple touch at specific screen coordinates and impersonate other apps using a “mimic” feature.
To evade detection for extended periods, the malware hides its icon from the home screen launcher after installation. Furthermore, the abuse of accessibility services allows Xenomorph to grant itself the necessary permissions to operate unhindered on compromised devices.
Previous iterations of the banking trojan disguised themselves as legitimate apps and utilities on the Google Play Store. However, the recent wave of attacks observed in mid-August 2023 has altered the modus operandi by distributing the apps through counterfeit sites offering Chrome browser updates.
The investigation further revealed that the infrastructure hosting the payload is also being used to distribute Windows stealer malware, such as Lumma C2 and RisePro, as well as a malware loader referred to as Private Loader. This indicates that the threat actors are targeting multiple operating systems.
ThreatFabric emphasized that Xenomorph remains an exceptionally dangerous Android banking malware, featuring a versatile and powerful ATS engine with multiple modules designed to support devices from various manufacturers.





Leave a comment