A concerning discovery has been made in the Google Play Store, where spyware disguised as modified versions of the popular messaging app Telegram has been found. These malicious apps were designed to gather sensitive information from compromised Android devices.
According to security researcher Igor Golovin from Kaspersky, these apps have nefarious features that capture and send names, user IDs, contacts, phone numbers, and chat messages to a server controlled by the attackers. This campaign has been given the codename “Evil Telegram” by the Russian cybersecurity company.
Before Google took them down, these apps had collectively been downloaded millions of times. The details of the malicious apps are as follows:
電報,紙飛機-TG繁體中文版 or 電報,小飛機-TG繁體中文版 (org.telegram.messenger.wab) – 10 million+ downloads
电报,纸飞机-TG简体中文版 (org.telegram.messenger.wob) – 50,000+ downloads
TG繁體中文版-電報,紙飛機 (org.telegram.messenger.wab) – 50,000+ downloads
电报,纸飞机-TG简体中文版 (org.tgcn.messenger.wob) – 10,000+ downloads
It is worth noting that the last app on the list, “Telegram – TG Uyghur,” specifically targets the Uyghur community.
One interesting detail is that the package name associated with the legitimate Play Store version of Telegram is “org.telegram.messenger,” while the package name for the APK file downloaded directly from Telegram’s website is “org.telegram.messenger.web.” The malicious apps used variations like “wab,” “wcb,” and “wob” in their package names, indicating an attempt to deceive users and evade detection by exploiting typosquatting techniques.
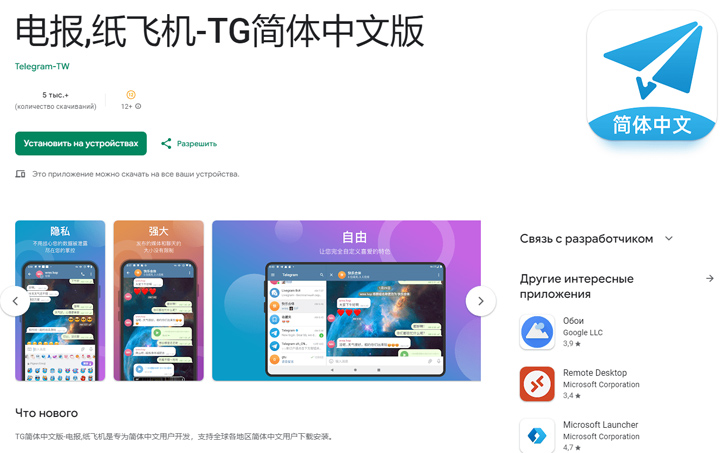
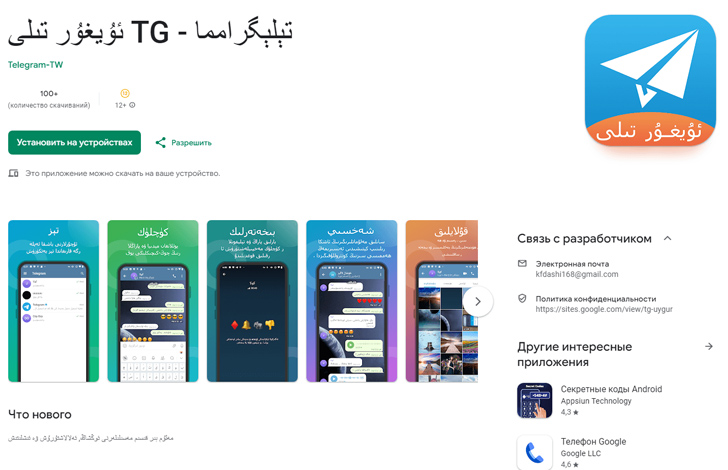
The malicious apps closely resemble the genuine Telegram app, with a localized interface that makes them appear legitimate. However, they contain an additional module that sets them apart, which unfortunately went unnoticed by the Google Play moderators.
This recent disclosure follows a previous discovery by ESET, revealing a BadBazaar malware campaign that exploited a rogue version of Telegram to gather chat backups. In March 2023, Slovak cybersecurity company ESET also uncovered similar copycat apps of Telegram and WhatsApp. These apps had clipper functionality, enabling them to intercept and modify wallet addresses in chat messages, redirecting cryptocurrency transfers to wallets controlled by the attackers.





Leave a comment